Introduction
Microsoft, Adobe and other software vendors regularly publish security updates (a.k.a patches), which fix security problems discovered in their software.
At CERN, these updates become available to all NICE computers within a process of a progressive monthly deployment. Updates are deployed using CMF. The deployment schedule is advertised using CERN Alerter.
CMF Centrally-managed machines
Windows 10/11 with Windows Automatic Update enabled (the default)
Starting with Windows 11 and extended to Windows 10, we consider the internal update mechanism to be more flexible and as reliable as CMF for the end users. Therefore, by default your machine will be configured to rely on MS Windows update. The default settings will perform as the following:
- Updates will be downloaded in the background when the machine is not used or lightly used as soon as they are available
- Nothing will be installed during active hours (by default those active hours are from 8h to 17h, but will adjust automatically to your usage)
- Pausing update feature will be disabled (for obvious security reason)
- If possible, pending updates will be installed during the night at 3h AM, except if the machine is running on batteries to avoid using it.
- New Feature updates (mainly new Windows Build version), will become available at CERN 120 days after their initial release to help improve stability.
- Quality updates (security patches, stability improvements):
- Dead line of 7 days after availability
- Grace period of 3 days after the dead line is reached
- Feature updates (mainly new windows build):
- Dead line of 21 days after availability
- Grace period of 7 days after the dead line is reached
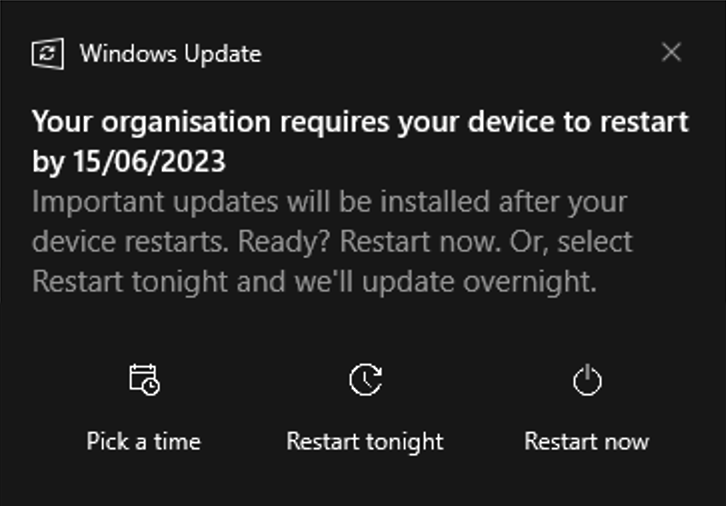
Windows 10/11 where Windows Automatic Update is not configured (very few exception / fallback mechanism)
A two-step approach is used. In the first step, new patches are notified to users, but aren't installed automatically. During this first step, users have complete control on the patching process and can postpone it. In the second step (which normally comes a couple of days after the first step), patch installation is mandatory. In most cases a reboot is needed and scheduled after the patches have been installed. This is necessary in order for the patches to be really installed and the computer to be protected against the security vulnerabilities.
Long-term off-site period (COVID-19 teleworking period included)
The normal configuration is made to get the updates using the internal CERN patching schedule. In case you know you are away for some time, please consult the following article KB0006582! to get your machine configured to download patches using Microsoft Windows Updates.
First step: user-controlled patch installation
This happens before patches are forced to install. You are notified that new patches are available when the CMF icon in the system tray (lower right of the screen) is pulsing in orange :

In this first step, the updates are not mandatory installed. You need to right-click on the icon and choose "Pending Actions":
To view which patches (or applications) need to be installed. This is like installing a regular application with CMF:
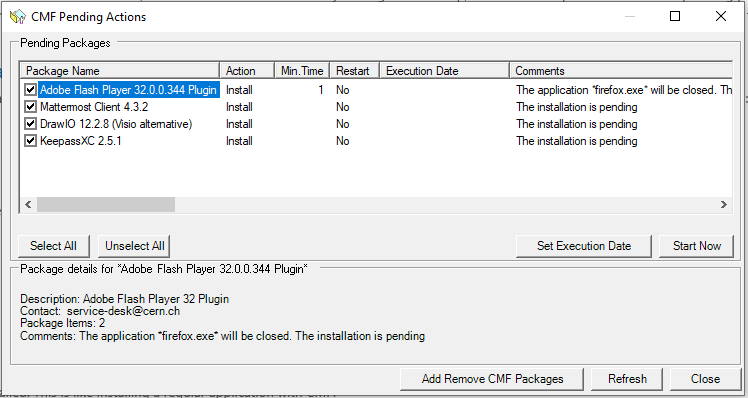
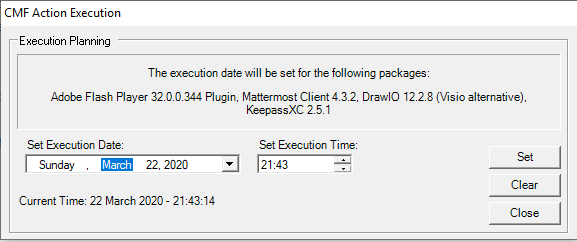
Users are advised to manually install the update - just by clicking the 'Start Now' button - as soon as possible. Please note the time of execution is specified as well as the restart condition. An execution date is also specified, which means the patches will be installed forcibly at that date. You can set another execution date by clicking 'Set Execution Date', but it can not be further than the date set on the package :
Second step : forced installation
In the second step of the patch deployment, installation begins automatically 5 minutes after the display of a warning pop-up. During this display you can manually postpone installation by 30 minutes by clicking 'Postpone 30 mins' :
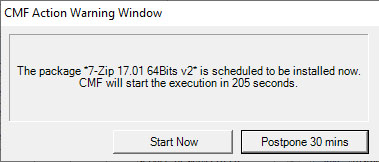
When you click 'Start Now' or when the delay expires, patch installation begins. You will see several windows opening and CMF balloons informing you of the update process. Please do not click the cancel buttons unless really needed.
Reboot after patch installation
At the end of installation, you are usually notified that the computer will reboot by the CMF icon pulsing in red (sometimes it may not be required to restart your computer) :

You are advised to close all opened applications and then right-click on the CMF icon, select 'The PC will be restarted..' and select 'Restart Now' :
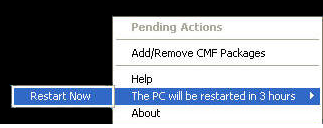
Anyway after expiration of the reboot delay, your computer will be rebooted and any open application will be forced to close, thus leading to possible data losses. That's why users are STRONGLY encouraged to install the security patches during the first phase of the deployment.
CMF Locally-managed machines
Create your own MS Monthly Patches
Starting January 2021, "MS Monthly Patches" packages distributed by CMF to local admins will become more efficient and include all missing updates on the machine at the time the package will be executed on the system. In the unlikely situation you would like to build your specific "MS Monthly Patches" to filter out some items known to disturb your systems, we created the following documentation to help you in this task: KB0007669
Windows 10/11 and before
Users that opted for locally-managed NSCs have the responsability of keeping their machines up-to-date. This process can be achieved by using the CMF Edit NSC page which is documented here.
Administrators of locally-managed NSCs are notified of the monthly updates one week after their release for CERN. To apply these patches the following steps may be followed:
-
Open the Package Collection tab, and at the bottom where the list of available packages is shown, ensure NICE NSS Is selected, and select (either individually or with
Ctrl/Cmd+Click) the packages that have been mentioned in the email. As an example, you may receive the following list:- MS Patches 20XX-XX
- PDF Xchange Pro V8 (x64) 8.0.XXX.0 (NICE)
-
With the above items selected, click on the Apply button at the bottom. This deployment type will force the applicable packages of each computer to apply.
You may as well apply these packages in another deployment model, but as you are the owner of this NSC, this is the quickest way to force them. The less intrusive way is to Publish+Install them. More information is available in the CMF documentation.
-
In addition (and optionally), click on the Edit button of each of these packages (which will all be shown at the bottom of the applied package collection list), set the checkbox of the Force Warning Date, and select a deadline date on which your computer will have to apply these packages. When this time is past, the packages will be forced on the computers without user’s consent.
Please note if you do not set a force warning date, the packages will be forcefully installed without consent on the machine.
-
Click on the Save button at the bottom and confirm your intent
-
Finally (and optionally), go to the Main Information tab, and set the checkbox for Run detection tool, and set the timestamp in the future with about 5 minutes, so that your computers will be asked by CMF to update their policies. Click on the Save button and we’re done!
Even if we don’t do this, the CMF agent may self-update quite soon.
At this point, all your computers should receive the applicable packages in CMF prompting them to install the updates.
Some packages (especially MS Patches from the list above), require a restart of the machine after it has been installed. In this case, the restart can be postponed for 5 hours after the installation.
Updating your computer without CMF
For computers not directly connected to CERN networks (home usage, travels, etc.), you cannot rely on CMF to install the updates.
For Microsoft updates, you can use the Windows Update feature built into the operating system. Normally on NICE Windows 10, the Automatic Updates functionality of Windows Update is disabled in order to avoid confusion with the CERN standard patching cycle and to allow a progressive deployment, that is used to protect CERN users in case of problems that an untested patch could cause in the CERN environment.
However, the Windows Update functionality remains available and the user can access it manually using:
Start Menu -> Programs -> Windows Update
Patch installation can be manually launched from there, which may be useful for for example during an occasional travel.
If a computer is regularly absent from the CERN network, the Automatic Updates functionality can be re-enabled for this computer using the Computer Accout Status page available at: https://winservices.web.cern.ch/winservices/Services/ComputerAccounts/ComputerAccountStatus7.aspx.